Authorization aware data fetching, cerbosctl improvements and more - Cerbos v0.12 Release
The latest version of Cerbos has been released with the focus of providing a smart mechanism to pass authorization logic down into your data storage layer, improvements to the cerbosctl, and a couple of enhancements to schema and test data.
Authorization aware data fetching with Query Planner (Experimental)
We are excited to introduce the new experimental Query Planner API to address a common use case in access control scenarios: filtering a list to retain only those items that a particular user has access to.
With traditional solutions for attribute-based authorization listing resources eg a list of user or blog posts is a tricky challenge as you would need to select entities out of a data store and then apply to filter based on permissions - this is inefficient as you may end up only filtering down to a handful (or even zero) entities to return to the user that they have access to.
With this release, you can now send a principal, action, and resource kind plus any available attributes to a new endpoint and obtain a tree representation of the minimal set of conditions that must be satisfied for that principal to be allowed to act on that resource kind.
This feature has been designed to be decoupled from any specific databases or query engine and instead provides a structured set of conditions that can be mapped to any source. We've heard from users of Cerbos and also our first-hand experience that in larger more complex systems data could be stored in a variety of systems (SQL, NoSQL, Cache, Key/Val, etc) and so operations needs to be fanned out and direct conditions applied to each lookup.
As an example, the following is a response from the Query Planner API on a system that has policies based on a resource's state and geography field. From this, it is possible to construct a conditional clause to be applied when querying the underlying data source.
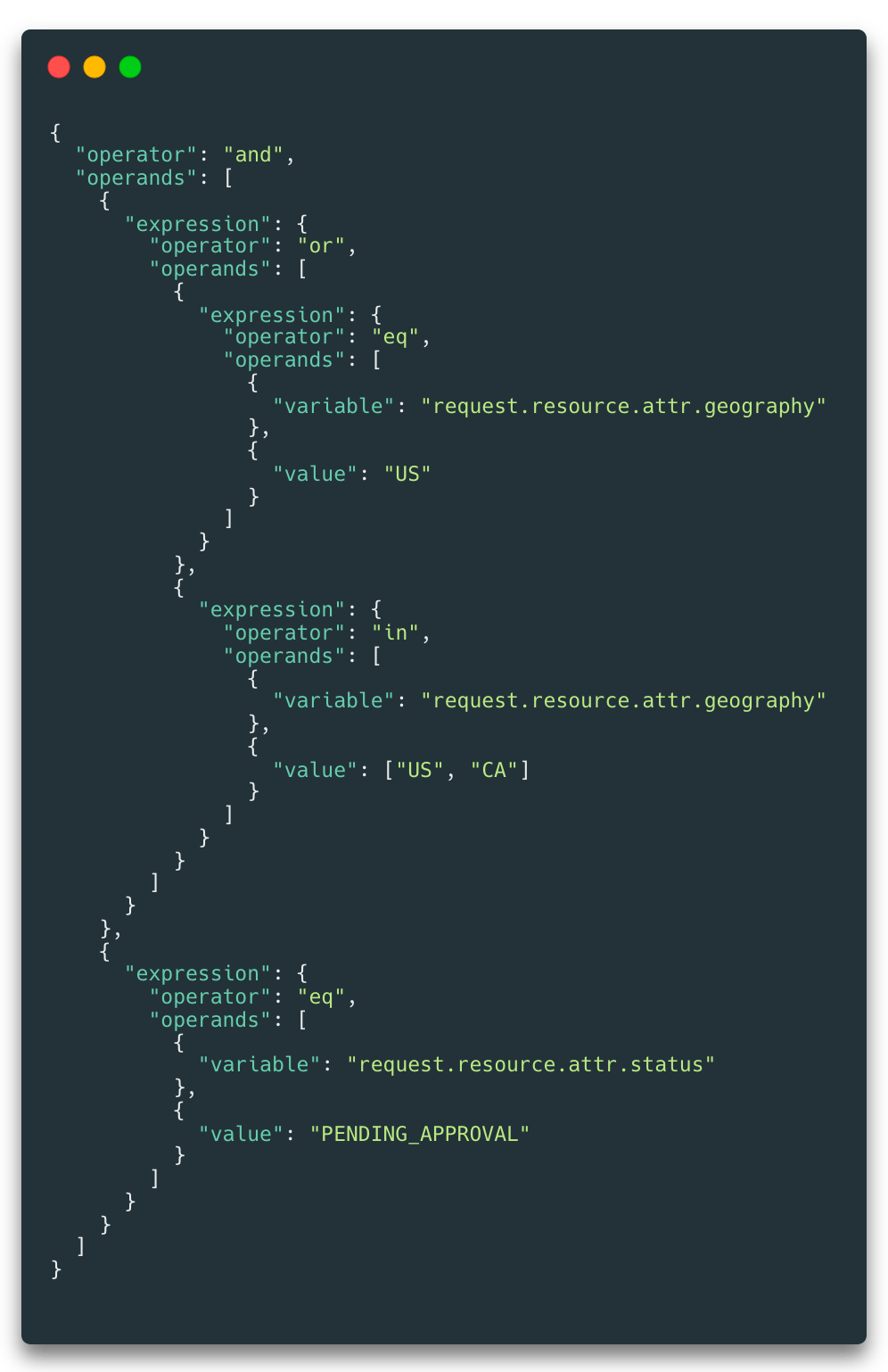
To aid usage, we are planning on releasing a set of libraries that will map this format into common syntax such as SQL or even ORMs like Prisma - more on this soon.
See Resources Query Plan for details about the new API. We will continue improving the underlying algorithms and the representation format in upcoming releases based on your feedback so please give it a go and let us know your use cases in our Slack community.
Revamped cerbosctl
Another exciting change in this release is the freshly revamped cerbosctl utility. In addition to being able to list and filter policies, you can now also list the schemas stored on the PDP.
We have streamlined the user experience to reflect the common CLI patterns provided by other, highly popular infrastructure management tools and thereby reduce the time required to become familiar with Cerbos. This is one of the rare cases where we felt that a breaking change was necessary to improve PDP resource usage and to make the user experience better. The cerbosctl list command has been replaced with cerbosctl get and the underlying Admin API endpoints have changed to provide policy listing and retrieval with much more predictable and constrained resource usage regardless of how many policies are stored in the policy repository.
See Admin API documentation and cerbosctl documentation for more details.
Optional Schema
After our previous release introducing schema validation one bit of feedback we had was around the ability to disable it for particular actions to support special cases such as resource creation where most of the necessary attributes might not be available to pass the validation step. This has now been added and can be read about here.
JWT Test Data
You can now use auxData in policy test suites to verify that the policies behave as you expect given various permutations of JWT data. When tests fail, you can inspect the evaluation graph of the request using the verbose flag to the test runner. See Validating and testing policies for details.
You can find the full release notes here and if you have any questions join our Slack community.
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
Recommended content

Mapping business requirements to authorization policy
eBook: Zero Trust for AI, securing MCP servers

Experiment, learn, and prototype with Cerbos Playground
eBook: How to adopt externalized authorization

Framework for evaluating authorization providers and solutions

Staying compliant – What you need to know
Subscribe to our newsletter
Join thousands of developers | Features and updates | 1x per month | No spam, just goodies.
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.
