Mapping business requirements to authorization policy for insurance
Many of us have insurance. If you own a car, house, a yacht, or say you are the world-famous guitarist Keith Richards of the Rolling Stones, your "hands" or perhaps just your "middle fingers" are insured for $1.6 million. According to Forbes, as of 2025, insurance fraud has claimed $306 billion from US consumers. The numbers tell a similar story in the rest of the world, and the money is eventually coming out of our pockets disguised as increased premiums. What are the primary reasons, and how can insurance companies utilize technology to combat fraud?
Insurance fraud happens for many reasons. Sometimes, agents or intermediaries forge claims or withholding policyholder payments. Other times policy holders deliberately invent loses to make false claims, known as hard fraud, or exaggerate legitimate claims by lying or omitting incident details, known as soft fraud.
There is some good news. Modern technology is well-positioned to combat insurance fraud. According to the US based National Association of Insurance Commissioners, fraud may actually be decreasing, due in part to the increased use of technology that helps detect fraudulent behaviours. Our focus in this article is to explore how modern authorization technologies are stepping in as the front line of defence against fraud in the insurance industry.
Insurance fraud can happen at any stage in the insurance lifecycle such as buying, using, selling, or underwriting policies.
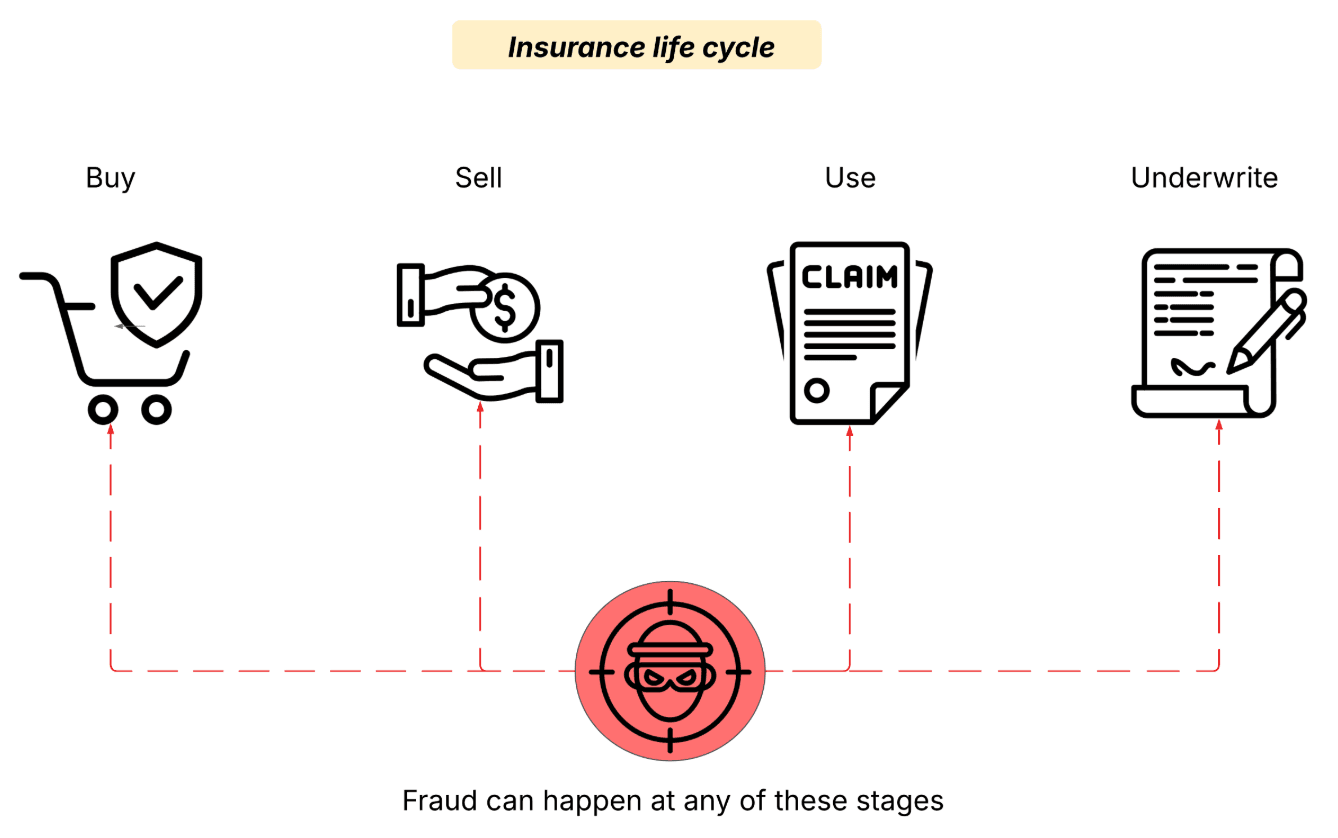
With today’s insurance processes being almost entirely digital, authorization has become an important fortress technology along with other cybersecurity software. In the following sections, we’ll explore how access control is applied across different scenarios in some of the most common types of insurance:
- Auto
- Life
- Property
Before we dive into examples, let's take a brief rundown on authorization because understanding this could change the way you think about insurance security forever.
The world of authorization
Authorization tries to solve the problem of "Who should have access to what?" and in the modern day it includes "under what conditions".
For example, you could have an authorization policy that says only staff of Customer Service Organization can access customer data (this is "Who has access to what?" part of the policy) during business hours (this is the "under what conditions" part of the policy).
Authorization challenges vary across industries, and in the insurance sector, they are shaped by a distinct set of factors and objectives, such as:
- Reduce fraud
- Prevent compliance violations
- Prevent data breaches
- Keep insurance premium increases under control
- Faster payout for successful claims
Let's keep in mind that the insurance industry holds some of the most sensitive customer data because of their nature of data collection. As well as that premiums are consistently under upward pressure due to increasing fraud and other factors.
Let us take a look at how authorization policies are composed, their building blocks are:
PrincipalThe actor performing the transaction, such as an underwriter.ActionThe act being performed, such as reading or modifying a policy.ResourceThe object on which the action is being performed, such as a policy or customer data.
The popular ways of implementing access control are by the use of RBAC, ABAC or PBAC.
| Model | Definition | Example |
|---|---|---|
| RBAC (Role-Based Access Control) | Relies on the role of the user to determine what actions are allowed on a resource. | If you are assigned the role “Claims Officer” → ALLOW approval of claims. |
| ABAC (Attribute-Based Access Control) | Relies on users' attributes to determine access permissions. | If claim.amount < 10000 AND user.region = claim.region AND time ∈ business_hours → ALLOW |
| PBAC (Policy-Based Access Control) | Combines the best of RBAC and ABAC; a natural evolution of both. Uses multiple data points within structured policies. |
|
In the above examples, we can see how each model approaches the same policy objective differently.
The limitations of RBAC quickly become evident. ABAC introduces flexibility by factoring in context (such as time of the day, location, etc.), while PBAC adds structure, making ABAC implementation more scalable and easier to govern. When policies are applied consistently across the company, they become manageable, and the most effective way to apply this is by centralizing them in a policy server. In one of my past projects, I saw companies attempt to manage transaction limits purely with roles. This led to role definitions like:
- Role 1: Approve claims under $10,000
- Role 2: Approve claims between $10,000–$20,000
- Role 3: Approve claims between $20,000–$30,000 …and so on.
This approach is really ineffective, creates unnecessary complexity, and also results in role explosion. Making governance difficult and inflexible over time. Let us explore how authorization using PBAC can help.
Authorization in action
We will explore three distinct scenarios across auto, life, and property insurance, each set at different stages of the insurance lifecycle, where PBAC policies can be applied to reduce the risk of insurance fraud. Through these examples, we will demonstrate how an authorization solution like Cerbos brings these policies to life.
Scenario 1: Auto insurance
Many countries have mandated auto insurances for people or organizations that own automobiles, especially third-party insurance, which covers damages caused to another vehicle in the event the primary owner is at fault. Let us explore an insurance buying scenario, where a Welsh resident, Mr. Kwame, has recently purchased a new large SUV, the Kia EV9, in the UK, and is applying for third-party insurance at one of the insurance providers, Castings Direct Insurance. Mrs. Jane, who works at the insurance company, reviews the application and is about to generate the policy with details of risk, coverage, and premium. The following is (1) an authorization policy statement, (2) the attributes of principal, action, and resource, and (3) a Cerbos policy example.
Authorization policy
Allow underwriting officers in the UK to generate third-party auto insurance policies if the application is complete, the coverage meets UK minimum standards, and fraud/risk checks have passed.
Factors used in the authorization policy
| Category | Attribute / Factor | Description / Purpose |
|---|---|---|
| User / Principal | role | Must be insurance_officer |
| department | Must belong to underwriting department |
|
| status | Must be an active employee | |
| Resource / Object | policy_type | Must be auto |
| demerit_points | Must be < 12 | |
| coverage | Must be third_party |
|
| vehicle_category | Must be in ["car", "suv", "motorcycle"] |
|
| owner_residency | Must be in ["Wales", "England", "Scotland", "Northern Ireland"] |
|
| application_status | Must be in ["submitted", "in_review"] |
|
| Contextual | country | Must be UK |
| third_party_mandatory | Must be true |
|
| fraud_check_passed | Must be true |
|
| access_channel | Must be internal_system |
|
| time_of_day | Must be within business hours, e.g., 09:00–17:00 |
|
| Action | create:policy | Allow for policy generation |
Cerbos policy
### Derived Role Policy
apiVersion: api.cerbos.dev/v1
derivedRoles:
name: insurance_underwriter_active
definitions:
- name: insurance_underwriter_active
parentRoles: ["insurance_officer"]
condition:
match:
all:
of:
- expr: request.principal.attr.department == "underwriting"
- expr: request.principal.attr.status == "active"
### Resource Policy
apiVersion: api.cerbos.dev/v1
resourcePolicy:
version: "default"
resource: "insurance_application"
importDerivedRoles:
- insurance_underwriter_active
constants:
local:
MAX_DEMERIT_POINTS: 12
VEHICLE_CATEGORIES: ["car", "suv", "motorcycle"]
UK_REGIONS: ["Wales", "England", "Scotland", "Northern Ireland"]
ALLOWED_STATUSES: ["submitted", "in_review"]
CHANNEL_INTERNAL: "internal_system"
WORKING_HOURS_START: "09:00"
WORKING_HOURS_END: "17:00"
rules:
- actions: ["create:policy"]
effect: EFFECT_ALLOW
derivedRoles: ["insurance_underwriter_active"]
condition:
match:
all:
of:
- expr: request.resource.attr.policy_type == "auto"
- expr: request.resource.attr.demerit_points < constants.MAX_DEMERIT_POINTS
- expr: request.resource.attr.coverage == "third_party"
- expr: request.resource.attr.vehicle_category in constants.VEHICLE_CATEGORIES
- expr: request.resource.attr.owner_residency in constants.UK_REGIONS
- expr: request.resource.attr.application_status in constants.ALLOWED_STATUSES
- expr: request.principal.attr.country == "UK"
- expr: request.resource.attr.third_party_mandatory == true
- expr: request.resource.attr.fraud_check_passed == true
- expr: request.resource.attr.access_channel == constants.CHANNEL_INTERNAL
This cerbos policy uses a combination of derived roles and resource policy. The derived role defines dynamic role based on user/principal attributes and resource policy defines rules for a specific resource, in our case its "insurance_application". It also uses local constants to improve reuse.
The above authorization policy helps in preventing multiple fraud activities in the insurance buying process:
- Prevents unauthorized employees or external parties from creating fraudulent policies. Ensures the user is a legitimate employee, preventing ghost accounts or former employees from generating policies.
- Restricts policies to valid vehicle categories in UK regions. Prevents fraudulent foreign or ineligible vehicles from being insured.
- Only applications in the submitted or in review state can proceed. Prevents bypassing review processes to issue fake policies.
- Ensures automated checks are completed before generation. Prevents obvious red-flag frauds (duplicate applications, high-risk profiles, etc).
In this case the Mr Kwame's 3rd party auto insurance application has been approved, and he is on the £40 monthly premium.
Scenario 2: Life insurance
The global life insurance market in 2025 is valued at $8 trillion according to Business Research Insights and is poised to grow further in the future. Unchecked fraudulent activities here could have catastrophic consequences for life insurance. In this scenario, we take a look at Mr. Wing, a Claims Officer working at a fictitious company, BIB Insurance in Hong Kong reviews an application from a claimant, Mrs. Lee, a Malaysian expat, a mother of two kids, who has recently lost her husband, aged 42 years, in an unfortunate car accident. She had filed a claim for $5 million on the life insurance policy her husband had taken with BIB Insurance 5 years ago. Let us look at a sample authorization policy that might be aiding Mr. Wing in policy review.
Authorization policy
Allow claims officers in Hong Kong to approve life insurance death claims exceeding $6 million if the claimant is the verified beneficiary, all required documentation is submitted, and no fraud indicators are present.
Factors used in the authorization policy
| Category | Attribute / Factor | Description / Purpose |
|---|---|---|
| User / Principal | role | Must be claims_officer |
| location | Must be Hong Kong |
|
| employment_status | Must be an active employee | |
| Resource / Object | claimant_id | Must match the principal ID (beneficiary verification) |
| policy_status | Must be active; policy will be closed upon claim approval |
|
| claim_amount | Must not exceed $6,000,000 | |
| documents_verified | Combined verification flag for all required documents (death certificate, police report, medical records, relationship proof) | |
| death_registered | Death registered with Hong Kong registry | |
| fraud_check_passed | Anti-fraud checks completed and passed | |
| Contextual | regulatory_compliance | Ensure the claim meets Hong Kong regulatory requirements |
| approval_sequence | At least 2 prior approvals completed before this current approval | |
| access_channel | Request must be made through authorized internal channels | |
| time_of_submission | Optional: verify claim submitted within allowable time frame after incident | |
| Action | approve:claim | Allow for approval of claim |
Cerbos policy
### Derived Role Policy
apiVersion: api.cerbos.dev/v1
derivedRoles:
name: claims_officer_hk_active
definitions:
- name: claims_officer_hk_active
parentRoles: ["claims_officer"]
condition:
match:
all:
of:
- expr: request.principal.attr.location == constants.HK_LOCATION
- expr: request.principal.attr.employment_status == "active"
constants:
local:
HK_LOCATION: "Hong Kong"
#### Resource Policy
apiVersion: api.cerbos.dev/v1
resourcePolicy:
version: "default"
resource: "life_insurance_claim"
importDerivedRoles:
- claims_officer_hk_active
constants:
local:
MAX_CLAIM_AMOUNT: 6000000
SUBMISSION_WINDOW: "4320h" # 180 days
CHANNEL_INTERNAL: "internal_system"
rules:
- actions: ["approve:claim"]
effect: EFFECT_ALLOW
derivedRoles: ["claims_officer_hk_active"]
condition:
match:
all:
of:
- expr: request.resource.attr.claimant_id == request.principal.id
- expr: request.resource.attr.policy_status == "active"
- expr: request.resource.attr.claim_amount <= constants.MAX_CLAIM_AMOUNT
- expr: request.resource.attr.documents_verified == true
- expr: request.resource.attr.death_registered == true
- expr: request.resource.attr.fraud_check_passed == true
- expr: request.resource.attr.regulatory_compliance == true
- expr: request.resource.attr.approval_sequence >= 2
- expr: request.resource.attr.access_channel == constants.CHANNEL_INTERNAL
Since the claim amount was substantial, Mr. Wing spent considerable time reviewing the case reviewing the documents to make sure the claim was genuine and legitimate. Apart from him checking the evidence, the authorization policy also checks multiple items as designed to ensure the claim is genuine.
Many of these checks would have taken considerable time if done manually. However, with most of the process automated, the authorization system performs reviews much faster. This leads to quicker payouts for BIB Insurance, higher customer satisfaction ratings, and stronger demand in Hong Kong. In this case, Mrs. Lee’s claim successfully passed all checks, and her $5 million payout was approved.
Scenario 3: Property insurance
In the land down under in Australia, the property market is one of the primary driving forces in the economy. According to Australian Bureau of Statistics, as of 2019-20, over 66% of Australians owned homes, and a recent survey found that about 11.8 million Australians hold Home and Contents insurance.
Imagine a scenario where Mr. Jericho, a long term resident in Sydney's northern beaches suburbs, has applied for $50,000 claim on his home and contents insurance, claiming his house roof has collapsed as a result of heavy rainfall. Let us see the authorization policy protecting homes in action.
Authorization policy
Allow claims officers to approve property insurance claims only if multi-factor conditions are met (valid police/fire reports, claim value within thresholds, claimant not recently in arrears, supporting evidence verified, and no red flags from fraud indicators). Otherwise, route the claim for secondary/managerial approval or fraud investigation.
Factors used in the authorization policy
| Category | Factor | Description / Purpose |
|---|---|---|
| User / Principal | Role = claims_officer, manager, fraud_investigator |
Ensures only authorized staff handle approvals and escalations |
| Experience level (junior vs senior officer) | Restricts junior staff from approving high-value or risky claims | |
| Resource / Object | Claim type = property (burglary, fire, storm) | Different fraud signals apply to different claim types |
| Claim amount > threshold (e.g., $50k / $100k) | High-value claims flagged for extra scrutiny | |
| Coverage start date vs claim date (e.g., < 90 days since policy start) | Detects suspiciously early claims after new policy issuance | |
| Supporting documents (police/fire reports, invoices, photos) | Prevents submission of fabricated or missing evidence | |
| Contextual | Cross-checks with external agencies (police, fire dept, weather bureau) | Confirms claim validity with independent authorities |
| Claimant financial distress (e.g., arrears or bankruptcy flag) | Identifies potential motive for fraud | |
| Number of prior claims filed by same claimant | Detects repeat fraudulent behaviour patterns | |
| Multi-level approval required (≥2 approvals before large payouts) | Adds governance and makes collusion harder | |
| Action | approve:claim | Allow for claim approval |
Cerbos policy
### Resource Policy
apiVersion: api.cerbos.dev/v1
resourcePolicy:
version: "2"
resource: "property_claim"
importDerivedRoles:
- claims_officer
constants:
local:
MAX_CLAIM_AMOUNT: 100000
MIN_COVERAGE_DAYS: 90
MAX_PRIOR_CLAIMS: 3
MIN_APPROVALS_REQUIRED: 2
rules:
- actions: ["approve:claim"]
effect: EFFECT_ALLOW
derivedRoles: ["claims_officer"]
condition:
match:
all:
of:
- expr: request.principal.attr.experience != "junior"
- expr: request.resource.attr.type == "property"
- expr: request.resource.attr.claim_amount <= constants.MAX_CLAIM_AMOUNT
- expr: request.resource.attr.coverage_duration_days > constants.MIN_COVERAGE_DAYS
- expr: request.resource.attr.has_valid_documents == true
- expr: request.resource.attr.police_report_verified == true
- expr: request.resource.attr.fire_report_verified == true || request.resource.attr.type != "fire"
- expr: request.resource.attr.weather_event_confirmed == true || request.resource.attr.type != "storm"
- expr: request.resource.attr.financial_distress_flag != true
- expr: request.resource.attr.prior_claims_count < constants.MAX_PRIOR_CLAIMS
- expr: request.resource.attr.approvals_count >= constants.MIN_APPROVALS_REQUIRED
In this scenario, the claims officer verifies the claim against the system, and the authorization engine blocks it from proceeding. Policy checks identify inconsistencies, such as the reported heavy rainfall date, which, when cross-referenced with Australia’s Bureau of Meteorology, shows no rainfall within three days of the claimed event. Further, a credit agency check reveals signs of financial distress in the applicant’s recent history. The claim is therefore flagged for further review. This case demonstrates how a centralized authorization solution like Cerbos can catch fraud attempts before they slip through.
Conclusion
Externalized authorization solutions such as Cerbos drive business value, allowing companies to focus on their core business. In the case of the insurance industry, it is to transform uncertainty into security, protect individuals and organizations from financial shocks, and enable economic growth.
In this article, we examined situations involving auto insurance, life insurance, and property insurance, and how authorization tech can assist claims officers take better decisions and automate many of the checks that would have traditionally taken a lot of time.
We have shown how policy models such as PBAC which are a natural evolution of ABAC provides a much powerful and contextual decision making capability than traditional RBAC, which only allows for a simple if member of "claims_officer" group than allow for policy approval.
From my experience working with multiple customers, I have observed a common trend in their digital transformation strategies, many are shifting their authentication capabilities 'to the left', centralizing them and moving them out of individual applications to an earlier stage in the transaction. With the rise of robust and reliable technologies like Cerbos, it is time to apply the same approach to authorization. Let's prevent compliance violations, stop data breaches, lower premiums, accelerate legitimate payouts, and reduce fraud by leveraging authorization. Let's move authorization left.
If you’re interested in implementing externalized authorization - try out Cerbos for free, or book a call with a Cerbos engineer to see how our solution can help streamline access control in your insurance organization.
To explore mapping business requirements to authorization policy for other domains - check out our foundational guide, or dive into these blogs specific to HR systems, MedTech, and FinTech.
FAQ
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
Recommended content

Mapping business requirements to authorization policy
eBook: Zero Trust for AI, securing MCP servers

Experiment, learn, and prototype with Cerbos Playground
eBook: How to adopt externalized authorization

Framework for evaluating authorization providers and solutions

Staying compliant – What you need to know
Subscribe to our newsletter
Join thousands of developers | Features and updates | 1x per month | No spam, just goodies.
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.
