AI agent security built on fine-grained authorization
Secure agentic workflows, RAG pipelines, and MCP servers with policy-driven access control and full decision logging.

AI agents introduce new security risks
Sensitive data leaks
AI agents may retrieve information beyond what the user is allowed to see.
Broken Zero Trust
Inherited or shared credentials break least-privilege and Zero Trust models.
Unauthorized actions
AI agents can perform high-impact operations, leading to errors, leaks, or abuse.
No audit logs
Without logs of AI agent actions, security teams can’t trace incidents or prove compliance.
Launch production-ready AI systems
Cerbos applies consistent authorization across your AI stack, controlling agent actions, filtering data access, and recording every decision. So your AI systems stay secure, compliant, and production-ready.
1
Define access control policies
Define context-aware access policies. Version, test, edit and roll out via Cerbos Hub.
2
Authorize agents, tools and data retrieval
Gate tool availability and filter every data call based on your authorization logic.
3
Log access decisions in the AI systems
Capture ALLOW and DENY decisions with reasons and policy version. Stream structured logs to your SIEM.
Build your AI security strategy
Shift AI security left. Use Cerbos to design, test, and enforce access controls before your models and agents reach production.
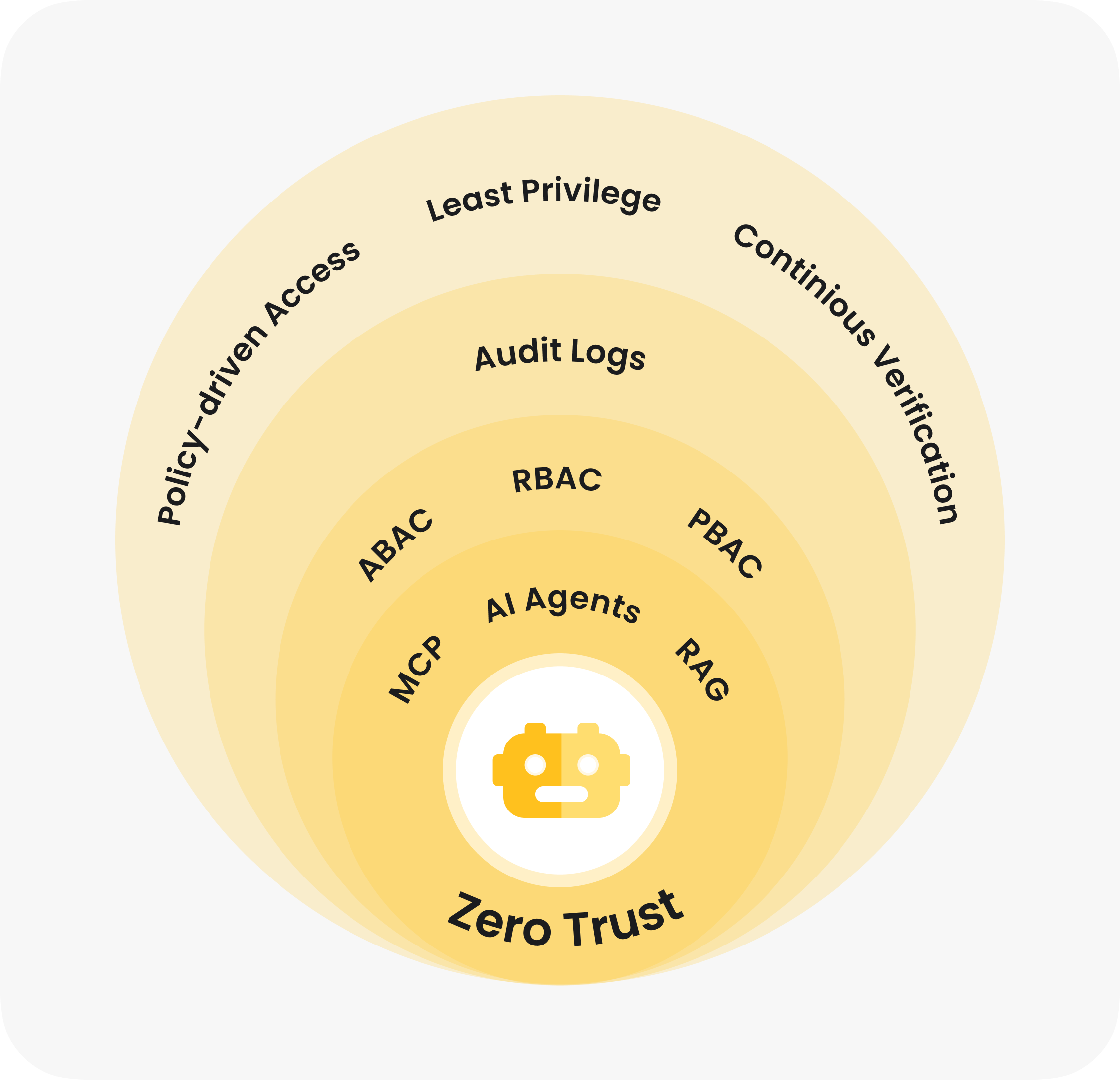
Enforce unified access for every identity
Apply RBAC, ABAC and PBAC consistently for MCP servers, RAG pipelines, AI agents and GenAI systems.
Align to Zero Trust principles
Zero Trust alignment so AI agents operate with least privilege and verified identities.
Authorize every action
Per-action authorization across APIs and downstream services to prevent impersonation and lateral movement.
Control your intelligent agents everywhere
Full control over AI agents in cloud, on prem or hybrid, embedded early in your AI lifecycle.
Follow AI security frameworks
Align authorization with emerging AI controls from OWASP LLM Top 10 and NIST AI RMF.
Security controls for every use case
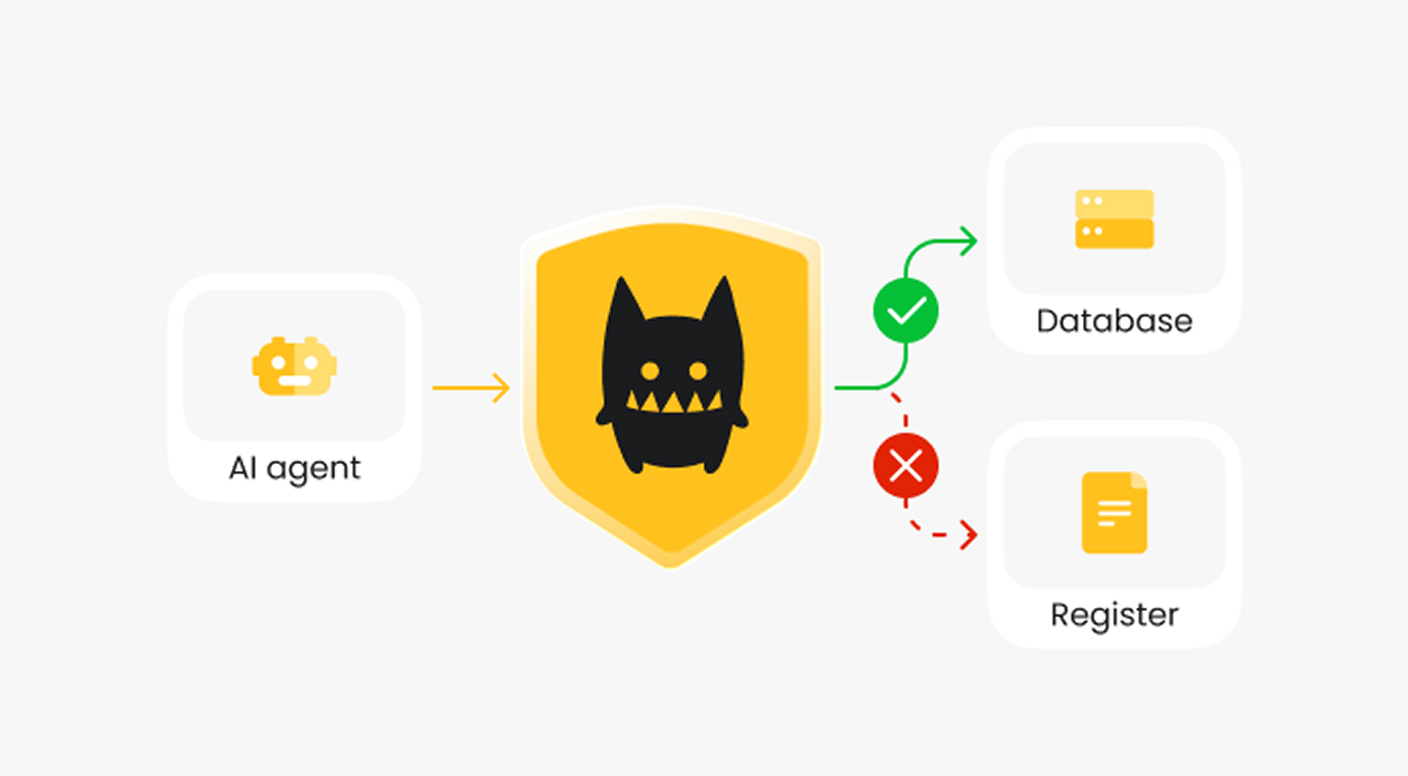
AI agent security
Control agent access to data and tools.
Prevent privilege escalation through the AI channel.
Define clear boundaries for agent actions, ensuring they operate within constraints.

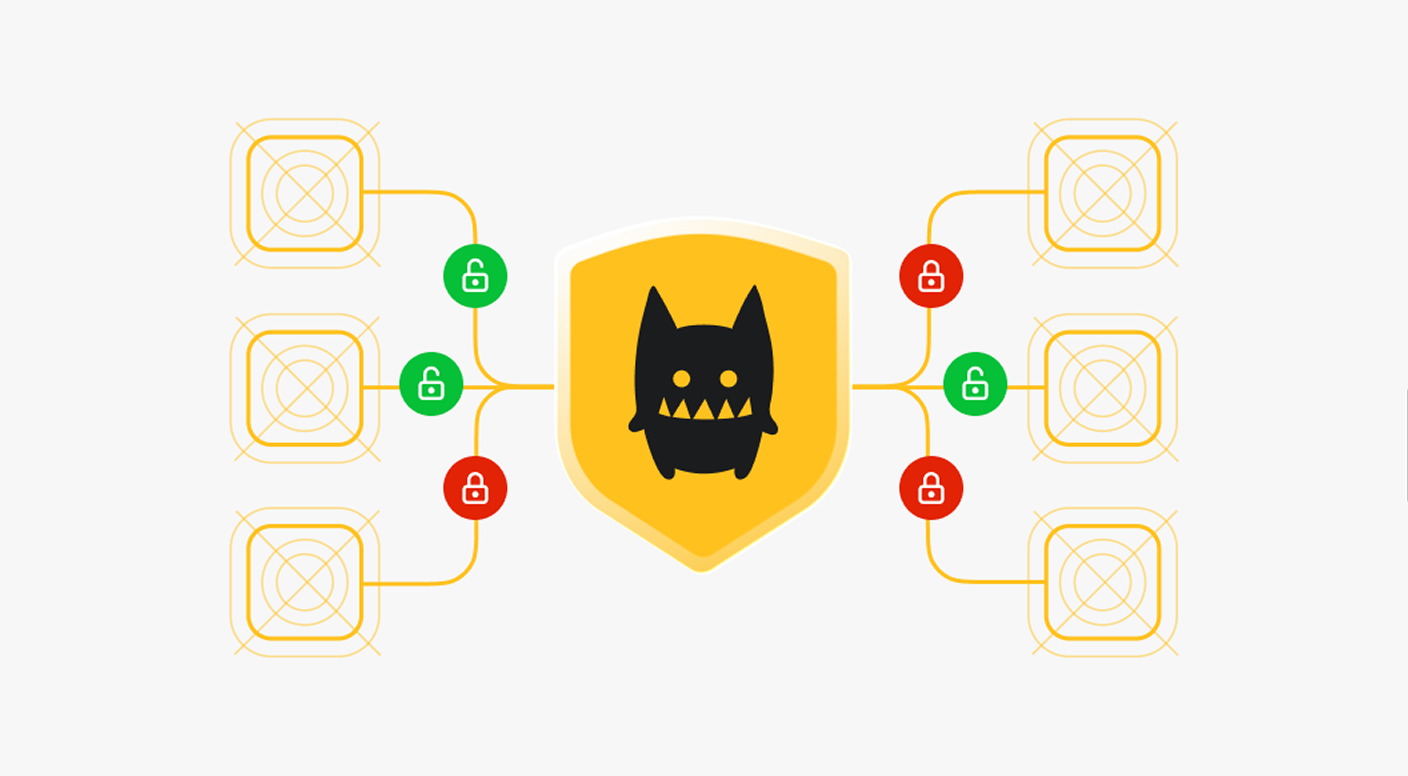
MCP server security
Centralize policy enforcement for MCP servers.
Manage permissions across tools and integrations.
Shrink the potential blast radius of security incidents.
Learn more
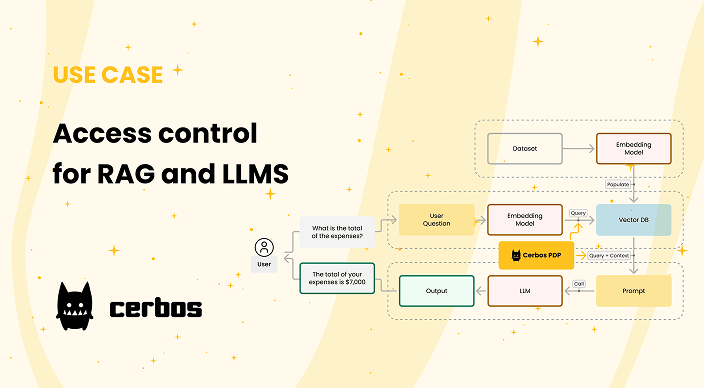
RAG authorization
Filter retrievals based on user permissions.
Protect vector stores and confidential data.
Control what context enters model prompts.
Learn more
Compliance ready with every authorization decision
SOC 2
SOC 3

HIPAA
ISO 27001

GDPR
FedRAMP
PCI DSS
Capture every decision for all identities
Log requests, actions, resources, access outcomes, and service-to-service authorization calls for both humans and machines.
Trace policy lineage
See the exact policy, version, and release behind each decision for complete traceability.
Monitor with context
Review detailed logs, policy versions, and real-time metrics across all PDPs and environments.
Simplify audits and compliance
Maintain centralized, structured logs on-premise to support audits and demonstrate readiness for FedRAMP, SOC 2&3, ISO 27001, HIPAA, PCI DSS, and GDPR.
Plug in and launch
Integrate with your AI stack in minutes
MCPs
Integrate Cerbos authorization with Fasten MCP and Anthropic MCP to control agent workflows at the orchestration layer.

Vector stores
Enforce policy-based access for embeddings and retrievals across FAISS, Pinecone, Weaviate, Chroma, and Qdrant.
AI infrastructure
Deploy Cerbos policies alongside your AI model APIs. Works with OpenAI, Anthropic, Groq, and other inference providers.
SDKs
Use Cerbos SDKs for languages like JS, Python, Go, Rust, Java, and .NET to authorize requests from your application code.



How teams use Cerbos for secure authorization



“We rely on Cerbos to make authorization decisions across the whole mesh - millions of times a day. And it’s fast. We don’t even think about it anymore. It just works.”

Rob Crowe
Principal Engineer @Utility Warehouse
Months of dev time reclaimed by replacing scattered access logic with Cerbos PDP.
Eliminated technical debt from authorization.
Why enterprises choose Cerbos
Time to market
100x faster launch
Deploy new roles and permissions instantly for RBAC, ABAC, PBAC.
Security
Reduce AI risk
Prevent AI over-permissioning and shadow access with Cerbos authorization.
ROI
90% cost reduction
Eliminate the need for custom-built authorization infrastructure.
Compliance
Audit-ready logs
Detect hidden permissions and compliance gaps across GDPR, SOC 2, HIPAA, ISO 27001.
Learn more

Ebook
Securing AI agents and non-human identities in enterprises

Webinar
Securing agentic AI in production

Ebook
Zero Trust for AI: Securing MCP Servers
Article
Implementing authorization in RAG-based AI systems with Cerbos
Article
MCP security & AI agent authorization.

Article
MCP permissions. Securing AI agent access to tools.
Build AI systems that are safe, compliant, and trustworthy
Enforce Zero Trust and least privilege across RAG, agents, tools and data retrieval with Cerbos.

Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.