Fintech
Fine grained authorization for fintech
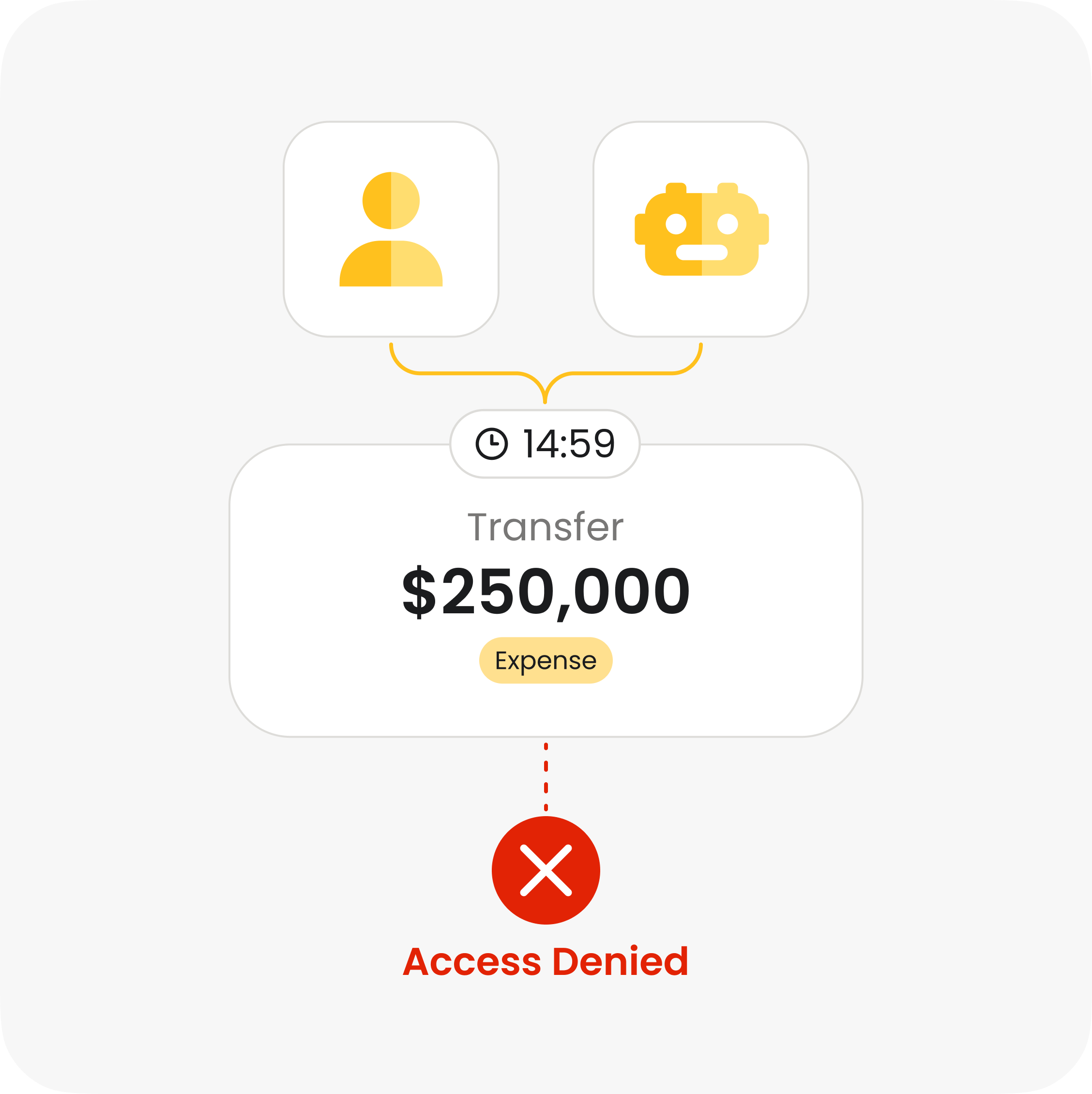
In fintech, every click moves real money. If you can’t prove who did what, when, and why, you’re exposed to fraud, insider abuse, and regulatory penalties.
Trusted by fintech teams building with security in mind


Streamline compliance
Meet audit requirements with centralized authorization logs.
Reduce development costs
Cut time spent building & maintaining authorization.
Update authorization instantly
Roll out new roles, limits, and financial controls.
Authorization for financial systems
Production ready authorization for your team
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Banking
Consistent, safe access for accounts and payments.
Payments
Control which agents can trigger transactions.
Lending and credit
Clear, explainable rules for approvals.
AI-driven finance
Limit agents to safe, auditable actions.
Core banking
Unified policy logic across services.
Wealth and trading
Restrict access to portfolios and trades.
BaaS
Isolated, per-client authorization control.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Why access control can’t be ignored
Security blind spot
Every transfer, approval, and data request depends on authorization logic.
Uncontrolled money movement
Over-permissive roles or missing real-time policy checks allow payment services to execute transfers.
Over broad data access
AI agents, APIs, and backend services often have broad access to customer PI & transaction data.
Untraceable access changes
When access rules are managed in different systems, no one can clearly see who changed permissions.
Slow compliance response
Every new AML or KYC rule requires code-level permission updates, delaying rollout and increasing audit risk.
Real breaches. Real companies. Real consequences.
90K accounts exposed
A broken session isolation bug caused users to see other users' account data, exposing PI and payment info due to failed authorization checks between sessions.
7M records leaked
An attacker abused overly broad internal support tool permissions, accessing sensitive user data without proper role-based access enforcement.
Zero Trust security at scale
Protect every financial action with Cerbos
Enforce fine grained, contextual, and continuous authorization across your financial systems. Protect payments, accounts, and AI-driven actions with strong access control.
1
Define access rules
Set clear, explainable policies for transfers, approvals, credit actions, sensitive data access, and AI-initiated operations — all outside your application code.
Set clear, explainable policies for transfers, approvals, credit actions, sensitive data access, and AI-initiated operations — all outside your application code.
2
Deploy Cerbos across your services
Run Cerbos PDP next to your core systems, payment processors, trading engines, decisioning services, or AI agents to enforce real-time, consistent authorization.
Run Cerbos PDP next to your core systems, payment processors, trading engines, decisioning services, or AI agents to enforce real-time, consistent authorization.
3
Integrate checks into money flows
Every transfer, trade, portfolio action, loan request, or AI-initiated event is evaluated against your policies before it’s allowed.
Every transfer, trade, portfolio action, loan request, or AI-initiated event is evaluated against your policies before it’s allowed.
4
Monitor and audit every decision
Get full visibility into who accessed what, which agent triggered which action, and why a financial decision was approved or denied.
Get full visibility into who accessed what, which agent triggered which action, and why a financial decision was approved or denied.
Compliance ready with every authorization decision
SOC 2
SOC 3

HIPAA

GDPR
ISO 27001
FedRAMP
PCI DSS
SOC 2
SOC 3

HIPAA

GDPR
ISO 27001
FedRAMP
PCI DSS
Capture every decision for all identities
Log requests, actions, resources, access outcomes, and service-to-service authorization calls for both humans and machines.
Trace policy lineage
See the exact policy, version, and release behind each decision for complete traceability and post-incident review.
Monitor with context
Review detailed logs, policy versions, and real-time metrics across all PDPs and environments.
Simplify audits and compliance
Maintain centralized, structured logs to support audits and demonstrate readiness for FedRAMP, SOC 2&3, ISO 27001, HIPAA, PCI DSS, and GDPR.
Fits into your IAM infrastructure
Connect with your stack, at an instance




How teams benefit from Cerbos for secure authorization



“We got the foundation set. Now we can scale and include more complex policies. And we can grow in the right direction and with the right security.”

Edgar Rivera
CEO @4gcapital
Saved per year by switching authorization services.
Policies are updated in minutes when requirements change.
How fintech teams use Cerbos

Saved $264k per year with scalable authorization
$264k saved per year vs. in-house build.
Policies are updated in minutes when requirements change.
Audit-ready compliance for ISO27001, SOC2, GDPR, PSD2, CCPA.

Modified product packaging in 10 minutes
Reduced hours of developer time to 10 minutes.
Eliminated technical debt from authorization.
Accelerated feature development and time to market.

Onboarded 3x more users with granular roles and permissions
Increased number of user roles available in the product.
Increased customer adoption with better user experience.
Secure and reliable access gating for sensitive resources.
Learn how to design authorization for financial systems
Article
Mapping business requirements to authorization policy for fintech

Webinar
Mastering authorization in Fintech
Guide
Designing an authorization model for an enterprise

Article
How Cerbos helped Nook build secure and extensible roles and permissions
Ebook
Building a scalable authorization system: a step-by-step blueprint
Ebook
How to adopt externalized authorization
Cerbos brings consistent authorization to your financial stack
Ensure every payment, account action, and AI-initiated operation is governed by fine grained, contextual authorization.
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.