Energy and Utilities
Access control for energy and utility platforms
Manage permissions across energy supply, billing, customer accounts, and multi service utility products.
Trusted by teams building with security in mind
Developer time savings
Remove duplicated authorization logic across thousands of services.
Flexible access rules
Update shared access rules across utility products.
Audit ready access
Trace and review authorization decisions centrally.
Authorization for enterprise systems
Production ready authorization for your team
Grid operations
Safe permissions for switching, routing, and load-balancing.
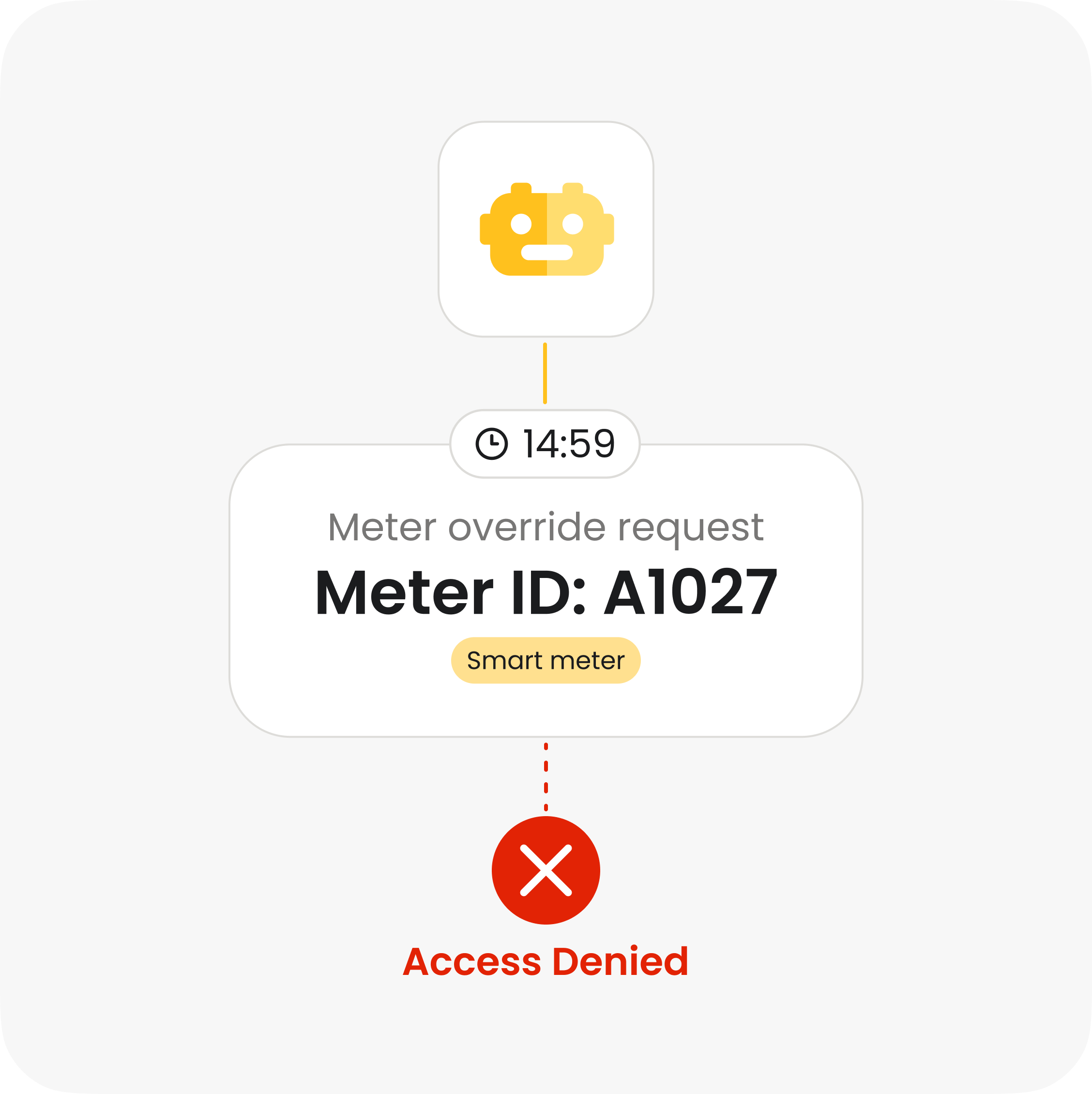
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Grid operations
Safe permissions for switching, routing, and load-balancing.
Meter data
Controlled access to read, edit, and export usage data.
Field technician permissions
Granular access for crews, contractors, and onsite work.
Customer account servicing
Secure updates to customer profiles, plans, and changes.
SCADA and IoT device actions
Least-privilege control of commands, configs, and telemetry.
Outage and incident response
Authorized workflows for reporting, escalation, and fixes.
Regulated enviroment
Run on-prem, air-gapped, hybrid with full auditability.
Billing and payments
Controlled adjustments to billing, credits, and payout actions.
Why access control can’t be ignored
Authorization blind spot
Critical actions across metering, billing, and customer systems rely on access decisions that are hard to audit centrally.
Uncontrolled system actions
Over permissive roles allow AI agents or systems to perform restricted operations.
Excessive data access
APIs and backend services often expose customer, usage, or billing data beyond what is required.
Untracked permission changes
When access rules live in multiple systems, it becomes unclear who changed permissions and when.
Slow operational changes
Updating access rules for new products or regulations requires code changes, slowing rollout and response.
Real breaches. Real companies. Real consequences.


1B identities exposed
API failed to enforce access controls, letting anyone retrieve national ID records without permission checks.
— Indane / Aadhaar, 2019

Critical infrastructure exposed
Internal database left open without access controls, leaking passwords and asset data.
— Pacific Gas & Electric, 2016
Zero Trust security at scale
Fine-grained authorization for Energy and Utilities
Enforces unified access decisions across customer systems, operational services, field tools, and machine driven workflows.
1
Define access rules
Author policies for grid operations, meter data access, field service actions, customer account changes, and partner integrations in a central policy layer.
Author policies for grid operations, meter data access, field service actions, customer account changes, and partner integrations in a central policy layer.
2
Deploy Cerbos across your systems
Run Cerbos next to customer platforms, operational services, data pipelines, and internal tools to enforce consistent authorization across distributed utility environments.
Run Cerbos next to customer platforms, operational services, data pipelines, and internal tools to enforce consistent authorization across distributed utility environments.
3
Enforce checks at runtime
Each request to read data, update customer records, trigger operational actions, or perform field operations is evaluated against policy in real time before execution.
Each request to read data, update customer records, trigger operational actions, or perform field operations is evaluated against policy in real time before execution.
4
Audit access decisions
Capture authorization outcomes with full context to support investigations, operational reviews, and regulatory audits across energy and utility systems.
Capture authorization outcomes with full context to support investigations, operational reviews, and regulatory audits across energy and utility systems.
Compliance-ready with every authorization decision
SOC 2
SOC 3

GDPR
ISO 27001
FedRAMP
PCI DSS
Capture every decision for all identities
Log requests, actions, resources, access outcomes, and service-to-service authorization calls for both humans and machines.
Trace policy lineage
See the exact policy, version, and release behind each decision for complete traceability and post-incident review.
Monitor with context
Review detailed logs, policy versions, and real-time metrics across all PDPs and environments.
Simplify audits and compliance
Maintain centralized, structured logs to support audits and demonstrate readiness for FedRAMP, SOC 2&3, ISO 27001, PCI DSS, and GDPR.
Fits into your IAM infrastructure
Connect with your stack, at an instance




How teams benefit from Cerbos for secure authorization



“We rely on Cerbos to make authorization decisions across the whole mesh - millions of times a day. And it’s fast. We don’t even think about it anymore. It just works.”

Rob Crowe
Principal Engineer @Utility Warehouse
Months of dev time reclaimed by replacing scattered access logic with Cerbos PDP.
Eliminated technical debt from authorization.
How Energy and Utility teams use Cerbos
Case study 1
Secured millions of human and machine identities with sub-millisecond authorization
NHI access secured at every hop, not just the perimeter.
User identity propagated throughout the service chain for full-context authorization.
Eliminated authorization bottlenecks and improved system reliability and audit at scale.
Case study 2
Unified authorization across 4,500+ services
Cut authorization maintenance from months to minutes for product teams.
Enhanced reliability and transparency for access control.
Eliminated technical debt from authorization.
Learn more about policy management
Guide
Designing an authorization model for an enterprise
Ebook
Building a scalable authorization system: a step-by-step blueprint
Ebook
How to adopt externalized authorization
Support complex utility services with consistent authorization
Manage access across energy, broadband, mobile, and billing systems as products and teams scale.
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.