Insurance
Authorization for regulated insurance systems
Control who can approve claims, change policies, and access sensitive customer and health data with fine grained authorization.
Trusted by fintech teams building with security in mind


Developer time savings
Reduce time spent implementing and updating authorization.
Flexible access rules
Adjust claim and policy access rules without code changes.
Audit ready access
Support regulatory reviews with auditable access decisions.
Authorization for insurance systems
Production ready authorization for your team
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
Claims handling
Rules for claim intake, review, and approval.
Underwriting decisions
Control changes to risk factors and premiums.
Policy servicing
Secure updates to coverage and beneficiaries.
Fraud investigation
Restrict access to suspicious cases and evidence.
Agent and broker network
Granular access for agents, brokers and adjusters.
Customer data protection
Controlled access to PII, health data, policy records.
Payments and disbursements
Boundaries for payouts and reimbursement actions.
AI-driven automation
Safe agent actions for quotes, claims, and servicing workflows.
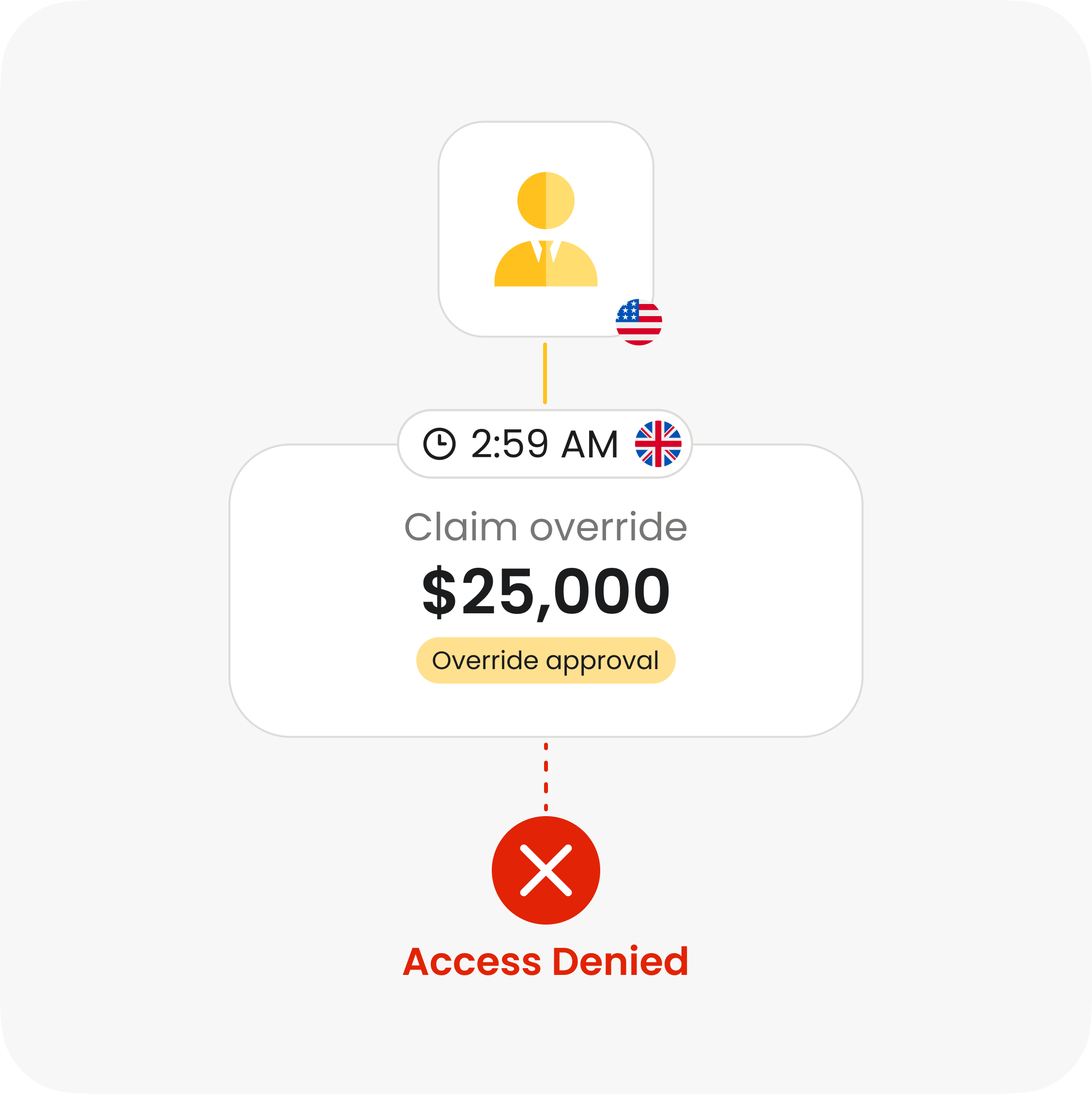
Why access control can’t be ignored
Authorization blind spots
Every claim update, policy change, and payout decision depends on authorization logic.
Unauthorized claim actions
Over permissive roles allow agents and claims systems to approve or override claims.
Sensitive data exposure
Customer and health data are often accessible beyond intended roles.
Untraceable access changes
Permission updates lack clear ownership and audit trails.
Delayed compliance controls
New rules take too long to enforce when access logic lives in code.
Real breaches. Real companies. Real consequences.

825K+ records leaked
APIs exposed personal data through public quote tools with no access checks.
— 8+ US auto insurers, 2020–2021

56.4M records at risk
APIs lacked object-level authorization, exposing full customer profiles.
— Policybazaar, 2022
Zero Trust security at scale
Fine grained authorization for insurance with Cerbos
Enterprise grade authorization for insurance systems, providing consistent allow or deny decisions for claims, policy changes, and payouts.
1
Define authorization policies
Model fine grained authorization for claims, policies, payouts, and sensitive data outside application code.
Model fine grained authorization for claims, policies, payouts, and sensitive data outside application code.
2
Deploy Cerbos PDPs
Run Cerbos next to insurance services to enforce consistent, real time authorization.
Run Cerbos next to insurance services to enforce consistent, real time authorization.
3
Enforce decisions everywhere
Evaluate every claim, policy, and payout action against authorization policies.
Evaluate every claim, policy, and payout action against authorization policies.
4
Audit every decision
Record who did what, why it was allowed, and which policy enforced it.
Record who did what, why it was allowed, and which policy enforced it.
Compliance-ready with every authorization decision
SOC 2
SOC 3

HIPAA

GDPR
ISO 27001
FedRAMP
PCI DSS
SOC 2
SOC 3

HIPAA

GDPR
ISO 27001
FedRAMP
PCI DSS
Capture every decision for all identities
Log access decisions for claim actions, policy updates, agent access, service-to-service calls across humans and machines.
Trace policy lineage
See the exact policy, version, and release behind each decision for complete traceability and post-incident review.
Monitor with context
Review detailed logs, policy versions, and real-time metrics across all PDPs and environments.
Simplify audits and compliance
Maintain centralized, structured logs to support audits and demonstrate readiness for FedRAMP, SOC 2&3, ISO 27001, HIPAA, PCI DSS, and GDPR.
Fits into your IAM infrastructure
Connect with your stack, at an instance




How teams benefit from Cerbos for secure authorization



“We got the foundation set. Now we can scale and include more complex policies. And we can grow in the right direction and with the right security.”

Edgar Rivera
CEO @4gcapital
Saved per year by switching authorization services.
Policies are updated in minutes when requirements change.
Learn more about policy management
Article
Mapping business requirements to authorization policy for fintech
Guide
Designing an authorization model for an enterprise
Ebook
Building a scalable authorization system: a step-by-step blueprint
Ebook
How to adopt externalized authorization
Protect critical insurance workflows with Cerbos
Enforce consistent access control across claims processing, policy changes, payouts, and sensitive customer data.
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.