Announcing ePDP Rules: Fine-grained control for embedded policy bundles
Since launching embedded PDPs, we've heard consistent feedback from teams using client-side authorization at scale. You wanted more control over bundle contents. You asked for tenant isolation in multi-tenant applications. You needed security controls for sensitive authorization logic.
Today, we're delivering on that feedback with ePDP Rules - a new way to configure exactly what policies are served to which clients, with enterprise-grade security built in.
What you asked for
Conversations with customers building browser applications, edge deployments, and multi-tenant SaaS platforms shaped this release. Three themes emerged:
-
"We need smaller bundles for browsers." Teams building SPAs and document editors wanted to serve only the policies relevant to end-user interactions, not the full policy set used by backend services.
-
"We need tenant isolation." Multi-tenant providers wanted each customer to receive only their scoped policies, improving both security posture and bundle performance.
-
"We need access controls." Security-conscious organizations wanted authentication and network restrictions before adopting embedded PDPs for sensitive authorization logic.
ePDP Rules address all three.
Introducing ePDP Rules
An ePDP rule is a named configuration that defines exactly how a policy bundle is built and served for a specific use case. Each deployment can have multiple rules - a minimal bundle for browsers, a full bundle for edge workers, a tenant-specific bundle for each customer. All from the same policy store.
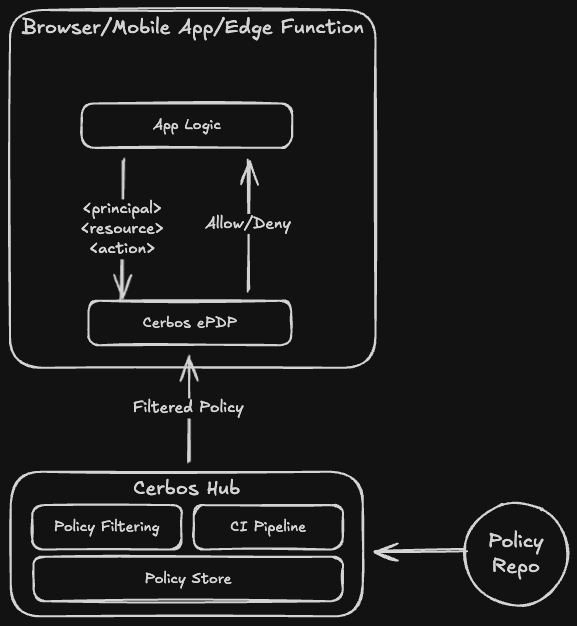
Policy filtering
Filter bundles to include only what each client needs:
- Resources and actions. Serve only
document:viewanddocument:editto your browser app, keepingdocument:deleteand admin resources server-side. - Scopes. Isolate tenant policies with static scopes (defined in the rule) or dynamic scopes (specified at fetch time).
- Roles. Exclude admin-only rules from end-user bundles.
- Versions. Support gradual rollouts or legacy client compatibility.
Security controls
Protect authorization logic with defense-in-depth:
- Client credential authentication. Require the same credentials used by service PDPs to download bundles.
- IP allowlists. Restrict downloads to corporate networks, CDN IPs, or known edge provider ranges.
Dynamic scopes for multi-tenant applications
For SaaS providers, dynamic scopes solve the tenant isolation challenge. Clients specify which tenant scope they need when fetching a bundle, and Cerbos Hub serves only the relevant policies. Requesting tenant-a.prod automatically includes ancestor scopes (tenant-a, root) while excluding everything else.
One deployment, multiple bundle profiles
Configure once, serve everywhere. A single deployment can define:
- A browser rule with minimal resources and actions, filtered to end-user roles
- An edge rule with full policies and IP restrictions for your CDN
- Per-tenant rules with dynamic scope filtering for customer-specific bundles
Each rule gets a stable identifier that client SDKs use to fetch the right bundle.
Unified platform, feature parity
With the upgrade, we have reached parity between the PDP and ePDP. Features like Query Plans now work in embedded environments. New PDP capabilities automatically benefit embedded deployments. One platform, your choice of deployment model.
Getting started
Sign up to Cerbos Hub to create your first ePDP rule. New deployments using Policy Stores automatically support ePDP Rules.
Full documentation is available at docs.cerbos.dev/cerbos-hub/deployments-epdp-rules.
What's next
This release establishes the foundation for embedded authorization at scale. Native mobile SDK support for iOS and Android is on the roadmap, with timelines driven by your feedback.
Log in to your Cerbos Hub workspace to create your first ePDP rule today. We'd love to hear how you're using client-side authorization, and what capabilities would make it even more powerful.
If you're new to Cerbos, try out Cerbos Hub or book a call with a Cerbos engineer to see how externalized authorization can streamline access control in your applications.
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
Recommended content

Mapping business requirements to authorization policy
eBook: Zero Trust for AI, securing MCP servers

Experiment, learn, and prototype with Cerbos Playground
eBook: How to adopt externalized authorization

Framework for evaluating authorization providers and solutions

Staying compliant – What you need to know
Subscribe to our newsletter
Join thousands of developers | Features and updates | 1x per month | No spam, just goodies.
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.