Authorization for GraphQL applications
Integrate Cerbos authorization service with your GraphQL application for fine-grained, low-maintenance access controls that scale from startup to enterprise.
Native GraphQL SDK
Checking authorization is as simple as calling a function in GraphQL which simplifies your code
Leverage context
Include request context attributes in the authorization logic to enable more contextual access controls
Keep up to date
Cerbos SDKs are kept up to date with the latest features and improvements
How Cerbos works with GraphQL
Building authorization logic inside GraphQL quickly becomes a maintenance burden. Hard-coded role checks scatter across controllers and middleware, and every permission change requires a code deploy.
Cerbos replaces scattered authorization logic with a single API call. You define fine-grained policies in YAML, and the Cerbos PDP evaluates them at request time using roles, attributes, and any context you provide.
With Cerbos your GraphQL application stays focused on business logic while authorization policies evolve independently, managed by product or security teams without touching code.
Building fine-grained access control for a GraphQL app
[#video#]
Common solutions for GraphQL roles and permissions
One of the many advantages of GraphQL is its flexibility. Unlike a REST API environment which will have only a single entry point for authorization, GraphQL can have multiple points of authorization for different levels of access, such as field resolvers or row-level data.
The dynamism this allows in your policies is awesome, but the amount of work required to maintain this type of authorization in code will bog you down. Here are the common ways to implement authorization in GraphQL.
- API-Wide Authorization: The simplest option is of course the “all-or-nothing” approach, in which your authorization allows or denies access to an entire API. This option is approprate for private environments where nothing is exposed to the public. However, it is inflexible to field-level access requirements or other modifications.
- Authorization in GraphQL Resolvers: GraphQL offers a way to delegate authorization to individual field resolvers. It places your authorization logic closer to user actions, allowing for more specific access restrictions. But in large systems you end up having to repeat code across multiple resolvers.
- Authorization in Models: This option helps solve the issue of repeating code, but makes your high-level rules more opaque, making it harder to prevent execution errors.
Advantages of the Cerbos GraphQL SDK for roles and permissions
Cerbos is a self-hosted, open source authorization service for GraphQL that allows you to offload tedious authorization decisions from backend services to a dedicated provider. This approach lets you decouple authorization logic as configuration scripts to ensure consistency between various services.
- Simplify your code
Call a single function instead of writing code everywhere. - Granular permissions
Configure ABAC, RBAC, row-level, and context-aware access policies in a single service instead of distributing complex logic throughout your application. - Scalability
Increase your load or add more roles and permissions without touching code. - Low maintenance
Policies are easy to update. Cerbos keeps the SDK up to date with lastest features and improvements.
How to integrate Cerbos with GraphQL
Step 1 - Configure a server
Define the port and location where you will store policies. You can then run Cerbos as a container or a binary.
Step 2 - Build roles and permissions in Cerbos
Define user roles and access policies for your application. The Cerbos Playground comes with pre-built policy examples to help you get started. also schedule a free workshop with our team, or join our Slack community to get help working out the right policy logic for your use case.
Step 3 - Integrate access control into your app using the GraphQL SDK
Once your policies are configured you can call Cerbos and perform permission checks from a GraphQL resolver. The GraphQL integration with Cerbos is demonstrated in full in our Github demo. And you can check out this video for a step-by-step tutorial.
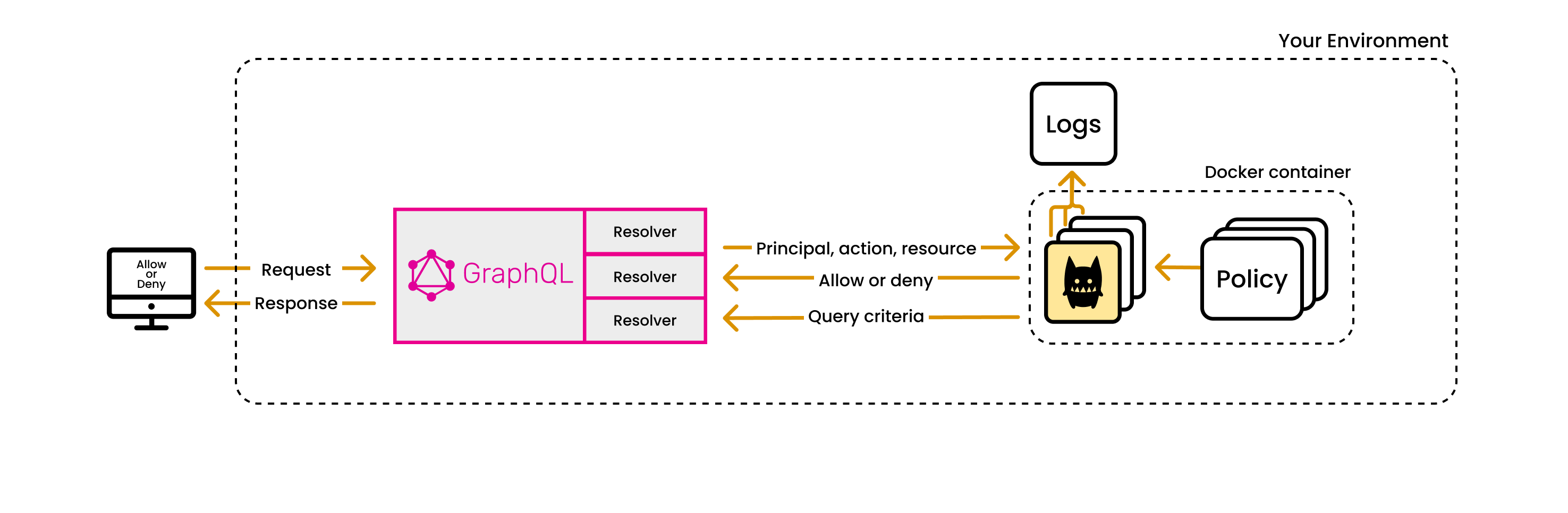
Step 4 - Iterate on roles and permissions in Cerbos without changing code.
Take a few minutes to update your policies in Cerbos. Permission checks performed by your GraphQL resolver continue unhindered with the updates applied automatically.
Get started
FAQ
How do I integrate Cerbos with GraphQL?
Cerbos integrates with GraphQL through a lightweight SDK or REST/gRPC API call. You replace hard-coded permission checks in your controllers or middleware with a single call to the Cerbos PDP, which evaluates your policies at request time.
Will Cerbos slow down my GraphQL application?
No. The Cerbos PDP runs alongside your application (as a sidecar or service) and delivers sub-millisecond authorization decisions. Because it's stateless and scales horizontally, it adds negligible latency to request processing.
Learn more about Cerbos
Related integrations
View all integrations →

Cerbos + GraphQL
- Single API call replaces hard-coded permission checks in GraphQL
- Policies updated independently of application deploys
- Authorization policies versioned and tested like source code
- Stateless PDP scales independently of the application
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.