Gartner IAM Summit 2025: Authorization maturity, AuthZEN momentum, and why identity security is expanding to every workload
The 2025 Gartner Identity and Access Management Summit in Grapevine underscored a decisive industry shift: authorization, workload identity, and policy based control have become foundational components of modern security architecture. As identity ecosystems expand beyond humans into services, autonomous agents, and distributed infrastructure, organizations are being pushed to rethink how access decisions are designed, enforced, and standardized.
Workload IAM: A unified taxonomy for the next era of identity
A standout moment came from Gartner’s Erik Wahlstrom, who introduced a maturing discipline: Workload IAM. Machine identities, containers, functions, VMs, services, ML pipelines, and increasingly AI agents have scaled far beyond what traditional IAM programs were designed to support. The result is a long tail of unmanaged or misunderstood credentials: API keys, tokens, certificates, and service accounts often treated as identities themselves.
Erik’s proposed solution was both simple and transformative. A consistent identity taxonomy where workloads become primary identity entities, and every associated credential is treated as an attached artifact, not an identity. This reframing eliminates one of the biggest sources of authorization drift: ambiguity about who or what is actually making a request.

Achieving industry alignment on this taxonomy will be essential. Authorization must operate consistently across legacy applications, SaaS products, in-house systems, cloud-native architectures, and AI-driven workloads. Without a shared understanding of identity, policy fragmentation and inconsistent enforcement become inevitable.
Modernizing authorization: centralize intent, externalize logic, standardize enforcement
Authorization modernization was another dominant theme across the conference. Hardcoded access logic continues to create bottlenecks in development cycles, gaps in auditability, and unpredictable security outcomes. Gartner highlighted the risks of “authorization sprawl”, multiple interpretations of access rules scattered across codebases, gateways, and infrastructure.
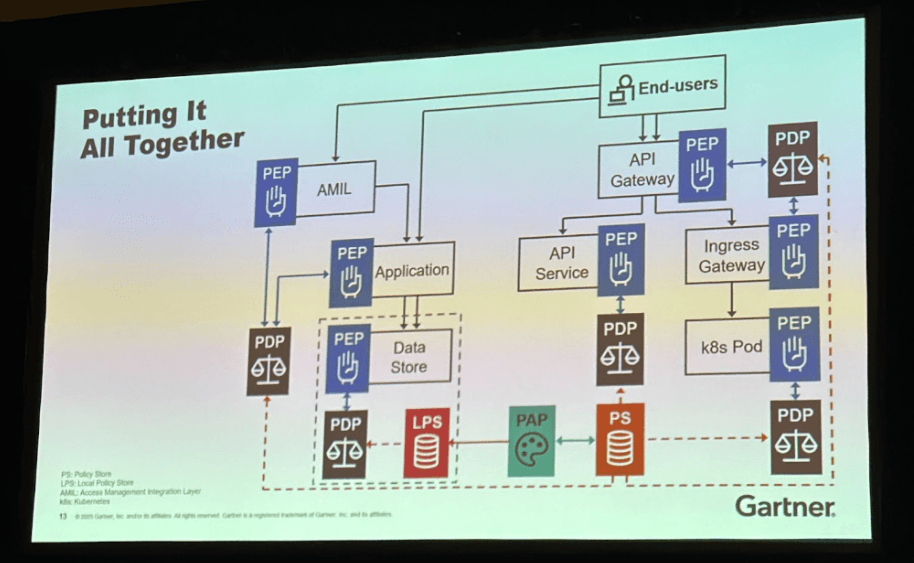
The modernization blueprint was clear:
- Centralize policy administration for governance and visibility
- Externalize policy evaluation for agility and consistency
- Decentralized enforcement for performance and resilience
- Make access decisions dynamic and context-aware
This combination mirrors the architecture long advocated by dedicated authorization engines, and aligns closely with where the market is heading as organizations adopt Zero Trust and platform engineering principles.
Policy based authorization in practice
Gartner continued the theme by emphasizing policy based authorization as the bridge between organizational intent and operational reality. Policies must be versioned, testable, explainable, and grounded in a well-understood fact model. Runtime authorization cannot succeed without knowing exactly which attributes and contextual signals matter.
Explicit comparisons across authorization engines, languages, and models revealed a predictable conclusion: no single model solves every problem. ABAC, ReBAC, role-based access control (RBAC), domain-specific rules, and hybrid approaches will coexist for the foreseeable future. The winners will be the teams that adopt structured policy patterns, effectively orchestrate multiple tools, and resist the temptation to let authorization logic drift back into application code.
Cerbos at the OpenID AuthZEN interop
One of the most anticipated moments of the conference was the OpenID AuthZEN interoperability session, this time focusing on how to integrate authorization at the IdP layer using the AuthZEN specification.
Cerbos took part both as a vendor and as a core implementer of the specification. Alex Olivier, Cerbos CPO and co-founder, is also an author of the AuthZEN specification and an active contributor to the working group driving it forward. This dual perspective, vendor, implementer, and standard author, positioned Cerbos uniquely in the interop.
The live demonstration featured implementers including Thales, Gluu, EmpoweredID, KeyCloak, and more. It was the first public demonstration of IdP gateway use cases powered by externalized authorization policies through a shared standard.

AuthZEN represents a significant milestone: the industry’s first realistic attempt at defining a common authorization API, much like OpenID Connect did for authentication. Its goal is to allow gateways, platforms, services, and applications to rely on a unified evaluation model regardless of the underlying engine. Work on the finalization of the specification has wrapped up and will be going out to voting by the OpenID membership very soon.
Why this matters
The message from Gartner this year: authorization has evolved from a backend control into a strategic identity infrastructure.
Key signals:
- Machine and workload identities require the same rigor, governance, and lifecycle management as human users
- Hardcoded authorization logic is technical debt that accumulates rapidly
- Policies should serve as the shared language between developers, security teams, and governance functions
- Standardized access patterns across applications, APIs, and platform layers reduce operational and security risk
- Open standards like AuthZEN are essential for creating composable, future-ready identity and authorization architectures
Cerbos was built for this shift. For teams designing runtime authorization, enabling multi-cloud policy governance, or securing identity-aware workloads and AI agents, Cerbos provides a fast, flexible, and standards-aligned path forward.
FAQ
Book a free Policy Workshop to discuss your requirements and get your first policy written by the Cerbos team
Recommended content

Mapping business requirements to authorization policy
eBook: Zero Trust for AI, securing MCP servers

Experiment, learn, and prototype with Cerbos Playground
eBook: How to adopt externalized authorization

Framework for evaluating authorization providers and solutions

Staying compliant – What you need to know
Subscribe to our newsletter
Join thousands of developers | Features and updates | 1x per month | No spam, just goodies.
Authorization for AI systems
By industry
By business requirement
Useful links
What is Cerbos?
Cerbos is an end-to-end enterprise authorization software for Zero Trust environments and AI-powered systems. It enforces fine-grained, contextual, and continuous authorization across apps, APIs, AI agents, MCP servers, services, and workloads.
Cerbos consists of an open-source Policy Decision Point, Enforcement Point integrations, and a centrally managed Policy Administration Plane (Cerbos Hub) that coordinates unified policy-based authorization across your architecture. Enforce least privilege & maintain full visibility into access decisions with Cerbos authorization.
